Bug #103149
openCSP prevents sitemap.xml inline CSS styles
0%
Description
Problem/Description¶
CSS Inline Styles in the auto generated sitemap.xml feature is blocked by Content Security Policy per default.
Affected: main, 13.0, 12.4
Acceptance Criteria¶
The styles should work without modifying CSP rules or the sitemap.xml template files.
BTW: what about a dedicated redmine category named "Content Security Policy"?
Files
 Updated by Timo Webler 2 months ago
Updated by Timo Webler 2 months ago
Our current workaround:
class PolicyMutatedEvent
{
protected string $sitemapPageType = '1533906435';
public function __invoke(\TYPO3\CMS\Core\Security\ContentSecurityPolicy\Event\PolicyMutatedEvent $event): void
{
$request = $this->getRequest();
if (
!$event->scope->isFrontendSite() ||
$request === null ||
$request->getAttribute('frontend.controller')?->getPageArguments()->getPageType() !== $this->sitemapPageType
) {
return;
}
$event->getCurrentPolicy()->set(
Directive::StyleSrcElem,
SourceKeyword::unsafeInline
);
}
protected function getRequest(): ?ServerRequestInterface
{
return $GLOBALS['TYPO3_REQUEST'];
}
}
 Updated by Benni Mack about 1 month ago
Updated by Benni Mack about 1 month ago
- Category changed from Frontend to Content Security Policy
 Updated by Timo Webler 23 days ago
Updated by Timo Webler 23 days ago
- Related to Bug #103567: Sitemap refuses to apply Stylesheet because of CSP added
 Updated by Oliver Hader 3 days ago
Updated by Oliver Hader 3 days ago
- Status changed from New to Under Review
- How to reproduce?
- What are the CSP headers being sent?
- What are the CSP violations being issued?
Besides that: Is it really relevant, that sitemap.xml supports styles when being shown in a browser? Or is it more like it should skip reports for sitemap.xml in case something is wrong there (but still block styles)?
 Updated by Timo Webler 3 days ago
Updated by Timo Webler 3 days ago
Oliver Hader wrote in #note-4:
- How to reproduce?
csp.yaml:
# Inherits default site-unspecific frontend policy mutations (enabled per default)
inheritDefault: true
mutations:
- mode: set
directive: 'default-src'
sources: ["'none'"]
- mode: set
directive: 'manifest-src'
sources: ["'self'"]
- mode: set
directive: 'img-src'
sources: ["'self'", "data:"]
- mode: set
directive: 'style-src'
sources: ["'self'", "'unsafe-inline'"]
- mode: set
directive: 'base-uri'
sources: ["'self'"]
- mode: set
directive: 'form-action'
sources: ["'self'"]
- mode: set
directive: 'media-src'
sources: ["'self'"]
- mode: set
directive: 'connect-src'
sources: ['self']
- mode: set
directive: 'script-src'
sources: ["'nonce-proxy'", "'self'"]
- What are the CSP headers being sent?
Content-Security-Policy: default-src 'none'; script-src 'nonce-JkAMWyZSCu6GhrHfwK6WLSPUIQC0vgunGZEmd-9RT1PpSpowF0zRfA' 'self' 'report-sample'; style-src-attr 'unsafe-inline' 'report-sample'; img-src 'self' data:; base-uri 'self'; frame-src 'self' *.youtube-nocookie.com *.youtube.com *.vimeo.com; style-src-elem 'self' 'nonce-JkAMWyZSCu6GhrHfwK6WLSPUIQC0vgunGZEmd-9RT1PpSpowF0zRfA' 'report-sample'; manifest-src 'self'; style-src 'self' 'unsafe-inline' 'report-sample'; form-action 'self'; media-src 'self'; connect-src self; report-uri https://exmaple.com
- What are the CSP violations being issued?
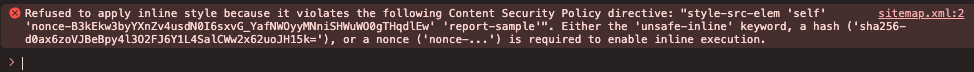
Besides that: Is it really relevant, that
sitemap.xmlsupports styles when being shown in a browser? Or is it more like it should skip reports forsitemap.xmlin case something is wrong there (but still block styles)?
Not really relevant. But TYPO3 deliver a stylesheet for that view and than it should work. Maybe remove the stylesheets for sitemap.xml as alternative solution.
 Updated by Oliver Hader 1 day ago
Updated by Oliver Hader 1 day ago
Thanks for the feedback, I was able to reproduce the behavior...
The resulting CSP violation looks like this:
{
"document-uri": "https://ip13.anyhost.it/?type=1533906435",
"referrer": "",
"violated-directive": "style-src-elem",
"effective-directive": "style-src-elem",
"original-policy": "default-src 'self'; script-src 'self' 'nonce-wdB5XPhMdnxXxfNpAsJGflt5UH0o_5-Z4ijHDwQLoQ-03gInUmWx_w' 'report-sample'; style-src-attr 'unsafe-inline' 'report-sample'; img-src 'self' data: *.ytimg.com *.vimeocdn.com; base-uri 'self'; frame-src 'self' *.youtube-nocookie.com *.youtube.com *.vimeo.com; style-src-elem 'self' 'nonce-wdB5XPhMdnxXxfNpAsJGflt5UH0o_5-Z4ijHDwQLoQ-03gInUmWx_w' 'report-sample'; report-uri https://ip13.anyhost.it/@http-reporting?csp=report&requestTime=1714503719476538",
"disposition": "enforce",
"blocked-uri": "inline",
"line-number": 2,
"source-file": "https://ip13.anyhost.it/",
"status-code": 200,
"script-sample": "body {\n font-fami"
}
script-sample gives an indication of what exactly caused the violation.
 Updated by Gerrit Code Review 1 day ago
Updated by Gerrit Code Review 1 day ago
Patch set 1 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Oliver Hader 1 day ago
Updated by Oliver Hader 1 day ago
- Related to Task #100887: Allow remote proxies to handle CSP nonce values added
 Updated by Oliver Hader 1 day ago
Updated by Oliver Hader 1 day ago
The patch at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099 is providing those hashes for the XSLT styles.
The hash value might be applied statically as well (sha256-d0ax6zoVJBeBpy4l3O2FJ6Y1L4SalCWw2x62uoJH15k=) - but I think this might be forgotten, in case the styles would be adjusted (even changing the formatting, whitespaces, etc. would require a new hash to be generated).
 Updated by Gerrit Code Review 1 day ago
Updated by Gerrit Code Review 1 day ago
Patch set 2 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099