Task #103722
closedDetected vulnerability with package 'enshrined/svg-sanitize'
100%
Description
The currently use of package enshrined/svg-sanitize with version constrain ^0.15.4 increase the risk score of TYPO3 projects.
The corresponding CVEs are
- https://github.com/darylldoyle/svg-sanitizer/security/advisories/GHSA-xrqq-wqh4-5hg2
- https://nvd.nist.gov/vuln/detail/CVE-2023-28426
Even the two mentioned CVEs are false-positive CVEs and should not bothered the project, these have an effect of the risk score.
The package should be updated to a newer version in order to solve this issue.
As of today, the current version available of this package is 0.18.0
Files
 Updated by Lars Tode 7 months ago
Updated by Lars Tode 7 months ago
- Related to Bug #100234: Incorporate tests of enshrined/svg-sanitize:v0.16.0 added
 Updated by Lars Tode 7 months ago
Updated by Lars Tode 7 months ago
- Related to Task #100233: Upgrade enshrined/svg-sanitize to ^0.16 added
 Updated by Oliver Hader 7 months ago
Updated by Oliver Hader 7 months ago
Lars Tode wrote:
The currently use of package
enshrined/svg-sanitizewith version constrain^0.15.4increase the risk score of TYPO3 projects.The corresponding CVEs are
- https://github.com/darylldoyle/svg-sanitizer/security/advisories/GHSA-xrqq-wqh4-5hg2
- https://nvd.nist.gov/vuln/detail/CVE-2023-28426
Even the two mentioned CVEs are false-positive CVEs and should not bothered the project, these have an effect of the risk score.
The package should be updated to a newer version in order to solve this issue.
As of today, the current version available of this package is
0.18.0
Updating to v0.18.0 seems to be fine by looking to the changes at https://github.com/darylldoyle/svg-sanitizer/compare/0.15.4...0.18.0
However, CVE-2023-28426 was rejected - thus, it must not have any negative impact on any "risk score".
Can you please provide a source/link to the service still assessing version 0.15.4 of the svg-sanitizer package as risky? Thanks in advance!
 Updated by Oliver Hader 7 months ago
Updated by Oliver Hader 7 months ago
https://github.com/darylldoyle/svg-sanitizer/issues/88 provides more context on the rejected CVE-2023-28426 → v0.15.4 was not vulnerable concerning the mentioned CVE
 Updated by Lars Tode 7 months ago
Updated by Lars Tode 7 months ago
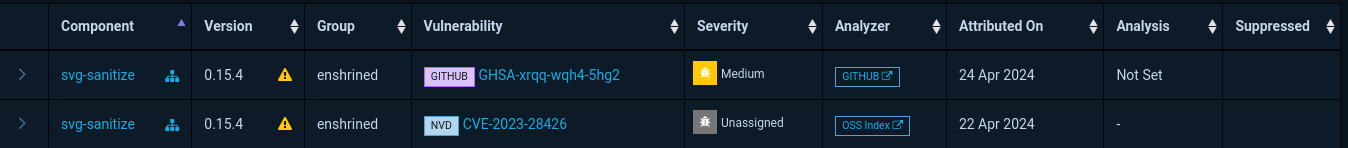
- File DependencyTrack.png DependencyTrack.png added
The GitHub Advisory still has a severity of medium.
The vulnerability will still be listed TYPO3 related projects.
The analysis is done via Dependency-Track
 Updated by Oliver Hader 7 months ago
· Edited
Updated by Oliver Hader 7 months ago
· Edited
- File 103722-1.png 103722-1.png added
- File 103722-2.png 103722-2.png added
https://github.com/darylldoyle/svg-sanitizer/security/advisories/GHSA-xrqq-wqh4-5hg2 is maintained only by the package maintainer, but not by GitHub, thus, it might be wrong or outdated.
https://github.com/advisories/GHSA-xrqq-wqh4-5hg2 is the correct advisory, managed by GitHub as CNA.
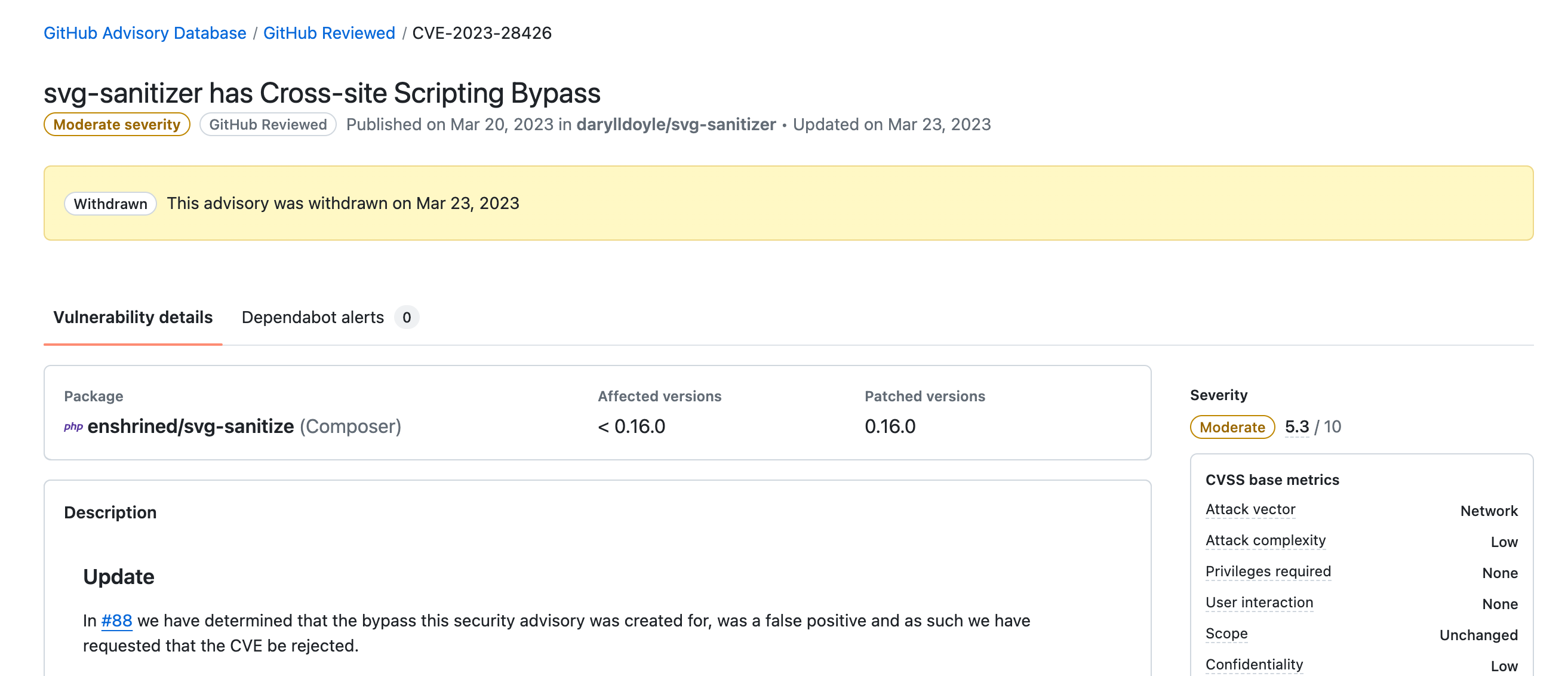
https://nvd.nist.gov/vuln/detail/CVE-2023-28426
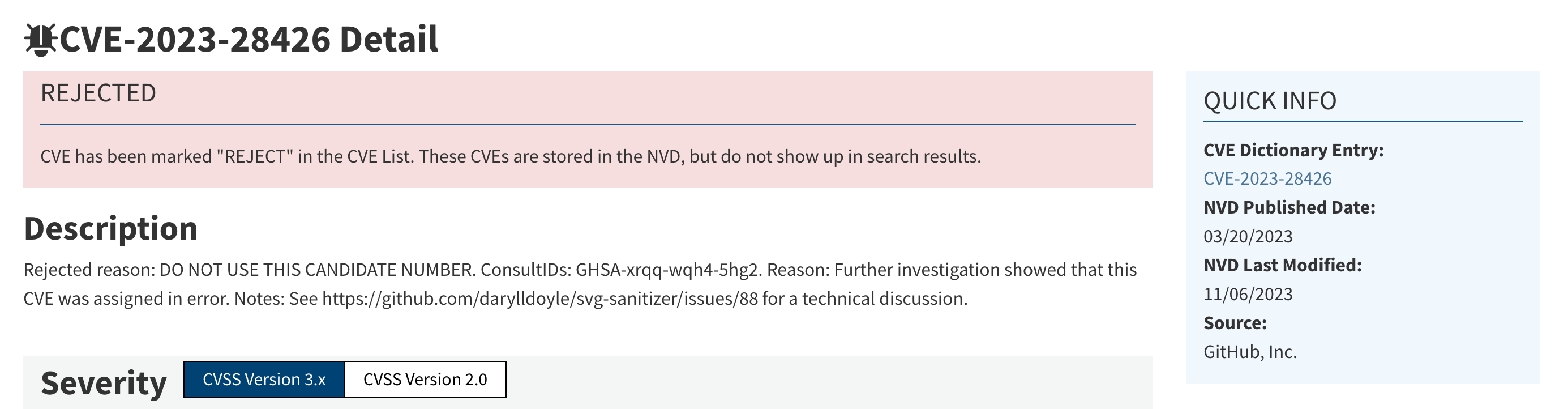
https://dependencytrack.org/ obviously does not consider the fact, that anybody(!) can create CVEs and that CVE can be rejected or disputed.
I'm sorry to say that, but that SBOM tool is based on fake, unverified or at least outdated information...
Again: The was no vulnerability in version 0.15.4 of composer package darylldoyle/svg-sanitizer
 Updated by Oliver Hader 7 months ago
Updated by Oliver Hader 7 months ago
Trying to reproduce that with DependencyTrack and PURL pkg:composer/enshrined/svg-sanitize@0.15.4 it get
- a vulnerability item with "unassigned severity"
- a reference to https://ossindex.sonatype.org/vulnerability/CVE-2023-28426?component-type=composer&component-name=enshrined%2Fsvg-sanitize&utm_source=dependency-track&utm_medium=integration&utm_content=v4.10.1 with a CVSS score of 5.3 (which is wrong, since the CVE was rejected)
- a risk score of 5 since version 0.15.4 is not the latest version 0.18.0 of the package
Conclusion¶
Watching and being aware of supply chain issues is an important thing - however, it is also important to understand how those results and information is retrieved and to double check the reports instead of relying only on numbers and risk scores.
 Updated by Lars Tode 7 months ago
Updated by Lars Tode 7 months ago
As mentioned in the ticket description, I am aware that this issue is a false positiv
Even the two mentioned CVEs are false-positive CVEs and should not bothered the project, these have an effect of the risk score.
The package itself should be updated within the TYPO3 core in order to avoid those messages.
 Updated by Gerrit Code Review 7 months ago
Updated by Gerrit Code Review 7 months ago
- Status changed from New to Under Review
Patch set 1 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84110
 Updated by Gerrit Code Review 7 months ago
Updated by Gerrit Code Review 7 months ago
Patch set 1 for branch 12.4 of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84137
 Updated by Gerrit Code Review 7 months ago
Updated by Gerrit Code Review 7 months ago
Patch set 1 for branch 11.5 of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84138
 Updated by Oliver Hader 7 months ago
Updated by Oliver Hader 7 months ago
- Status changed from Under Review to Resolved
- % Done changed from 0 to 100
Applied in changeset 4361d3ca256050d5e1c51e17cdc8ac1c0bdaa72c.
 Updated by Christian Kuhn 3 months ago
Updated by Christian Kuhn 3 months ago
- Related to Bug #104611: Raise enshrined/svg-sanitize:^0.19.0 added