Bug #91993
closedOfficial documentation and actual implementation of AuthenticationService is fatally mismatching
0%
Description
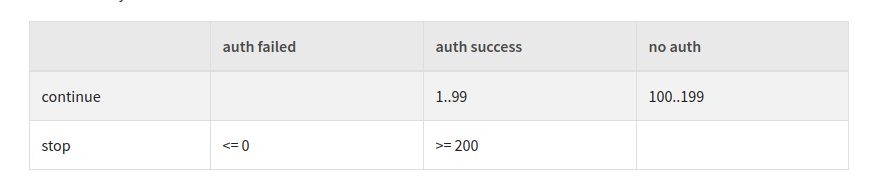
The documentation states:
a value of 0 or a value of 100 or more indicates that the authentication has failed, but that further services should keep trying.
But the actual code treats 0 like totally failed, to NOT try further (it checks the return code for greater 0 not greater--or-equal 0):
foreach ($this->getAuthServices($subType, $loginData, $authInfo) as $serviceObj) {
if (($ret = $serviceObj->authUser($tempuser)) > 0) {
// If the service returns >=200 then no more checking is needed - useful for IP checking without password
if ((int)$ret >= 200) {
$authenticated = true;
break;
}
if ((int)$ret >= 100) {
} else {
$authenticated = true;
}
} else {
$authenticated = false;
break;
}
}
if ($authenticated) {
// Leave foreach() because a user is authenticated
break;
}
Luckily we did not trust the docs blindly in one of our projects but checked the core code first - else we had run in severe problems.
This must be fixed one way or the other.
IMHO, the docs should be correct. It must be possible to override a failed authentication by custom code. This is not possible if the service chain just ends hard.
Currently overriding failed core auth is only possible if an unknown hash algorithm is used.
Our use cas ist this:- If a user is not "blocked" (check in a custom auth service with priortity >50), then just run core auth, else fail hard (negative return).
- if not blocked and core auth fails (wrong password given) we increase a failed login attempt counter and eventually block the user (custom auth service with priority <50)
- when core auth succeeds we unblock the user in the custom auth with priotity <50
This is not possible currently.
Files