Feature #87423
closedEpic #87417: Integrate proper Content Security Policy (CSP) handling
Integrate CSP management module
100%
Description
In oder to grant access, configure behavior and monitor configuration flaws or violations (e.g. of 3rd party extensions) a content security policy management module shall be integrated.
- grant/revoke access (based on manifest)
- configure content security level (predefined/presets)
- log of recent violations with UI filter capabilities (search for URI, type, date/time, ...)
Test-Extension¶
Files
 Updated by Oliver Hader about 3 years ago
Updated by Oliver Hader about 3 years ago
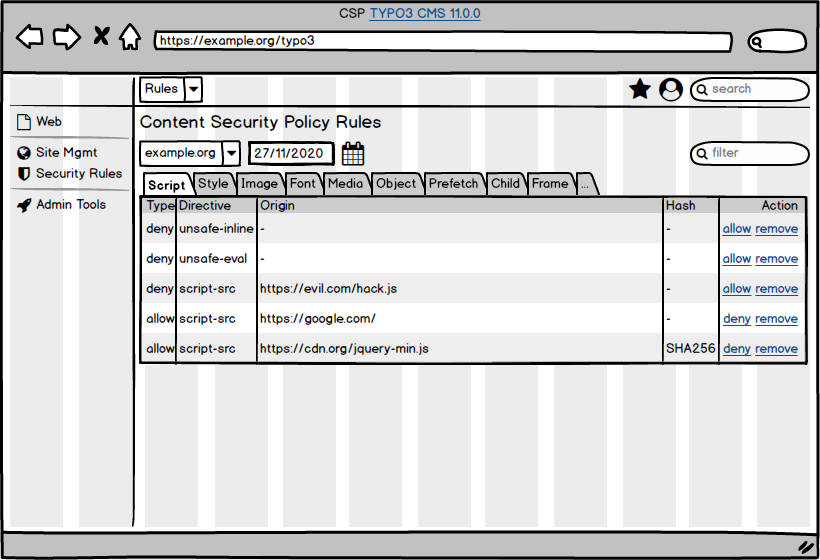
- File mockup_Rules.png mockup_Rules.png added
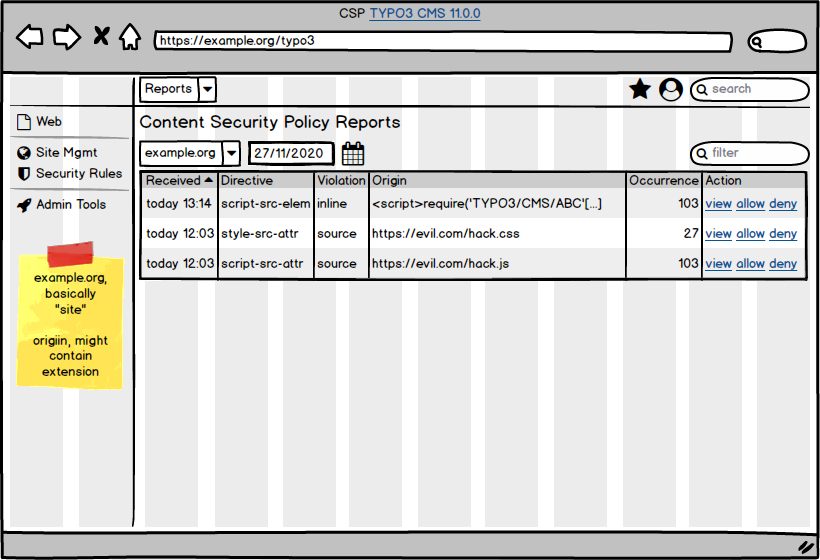
- File mockup_Reports.png mockup_Reports.png added
- File typo3_csp.bmpr typo3_csp.bmpr added
- Description updated (diff)
 Updated by Oliver Hader over 2 years ago
Updated by Oliver Hader over 2 years ago
- Target version changed from Candidate for Major Version to 12 LTS
 Updated by Rachel Foucard over 2 years ago
Updated by Rachel Foucard over 2 years ago
Hi Oliver,
I dreamed about it!
I also wonder if it would technically possible to get a understandable message (back or front) when a simple editor add an HTML content and get no result because of CSP? something like "This content can't be displayed because some security are blocking external urls, please ask your administrator to approve them first, blabla..."
Rachel
 Updated by Oliver Hader over 2 years ago
Updated by Oliver Hader over 2 years ago
Rachel Foucard wrote in #note-4:
I also wonder if it would technically possible to get a understandable message (back or front) when a simple editor add an HTML content and get no result because of CSP? something like "This content can't be displayed because some security are blocking external urls, please ask your administrator to approve them first, blabla..."
Technically it's possible to handle these "CSP violations" with the corresponding event in JavaScript, e.g. see https://developer.mozilla.org/en-US/docs/Web/API/SecurityPolicyViolationEvent for details. I used this technique in a proof-of-concept prototype (end of 2019) to collect violations during runtime.
Another possibility would be to use reporting endpoints (like Sentry or similar services) which is more generic, since not all application states (mainly JavaScript states) are submitted, e.g. see https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy/report-to for details.
 Updated by Oliver Hader over 1 year ago
Updated by Oliver Hader over 1 year ago
- Has duplicate Feature #100056: Introduce Content Security Policy reporting & inspection added
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
- Status changed from Accepted to Under Review
Patch set 13 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Oliver Hader over 1 year ago
Updated by Oliver Hader over 1 year ago
- Related to Feature #87421: Integrate CSP reporting endpoint added
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 14 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 15 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 16 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 17 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 18 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 19 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 20 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 21 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 22 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 23 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 24 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 25 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 26 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Gerrit Code Review over 1 year ago
Updated by Gerrit Code Review over 1 year ago
Patch set 27 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/77998
 Updated by Oliver Hader over 1 year ago
Updated by Oliver Hader over 1 year ago
- Status changed from Under Review to Resolved
- % Done changed from 0 to 100
Applied in changeset 94bcbf0fac160732cf90021d60f08fcb41952a50.
 Updated by Oliver Hader over 1 year ago
Updated by Oliver Hader over 1 year ago
Rachel Foucard wrote in #note-4:
I also wonder if it would technically possible to get a understandable message (back or front) when a simple editor add an HTML content and get no result because of CSP? something like "This content can't be displayed because some security are blocking external urls, please ask your administrator to approve them first, blabla..."
Technically it's possible to show a dialog whenever CSP violations occur. However, it's not known and cannot be inferred what this violation causes to the visible representation. Thus, it's not known whether e.g. a site visitor tracker (Google, Matomo, ...) or a lightbox (from external CDN) has been blocked.
 Updated by Chris Müller over 1 year ago
Updated by Chris Müller over 1 year ago
- Related to Task #100534: Avoid PHP deprecation in CSP report added
 Updated by Chris Müller over 1 year ago
Updated by Chris Müller over 1 year ago
- Related to Task #100535: CSP module: On small browser size the UX of the details view could be improved added
 Updated by Oliver Hader over 1 year ago
Updated by Oliver Hader over 1 year ago
- Related to deleted (Task #100534: Avoid PHP deprecation in CSP report)
 Updated by Chris Müller over 1 year ago
Updated by Chris Müller over 1 year ago
- Related to Task #100616: Add docheader buttons to CSP module added
 Updated by Chris Müller over 1 year ago
Updated by Chris Müller over 1 year ago
- Related to Bug #100618: CSP module: Mute and delete of violations do not work added