Bug #93035
closedfileadmin/.htaccess prevents Safari from accessing PDF files (after latest security update)
100%
Description
It seems that https://github.com/TYPO3/TYPO3.CMS/commit/444b05e6948829b7fb9e33cdb546f4cd9ec0ac9e or #92835 introduced a .htaccess file in fileadmin folder.
For whatever reason Safari on Desktop (e.g. version 14) blocks requests to pdf when this header is set (TYPO3 version 9.5.23):
Content-Security Policy: object-src 'none'
Here is s a german discussion about the Safari issue: https://www.apfeltalk.de/community/threads/safari-blockiert-ploetzlich-alle-pdfs.555787/
Files
 Updated by Oliver Hader almost 4 years ago
Updated by Oliver Hader almost 4 years ago
(posted by @Peter Schuler at https://typo3.slack.com/archives/C0K5MU94J/p1605704844039500)
I dug a bit: to enable the plugin in Safari for my testcase object-src 'self'; is necessary, to drop console warnings additionally style-src 'unsafe-inline' thus resulting in:
<IfModule mod_headers.c> Header set Content-Security-Policy "default-src 'self'; style-src 'unsafe-inline'; script-src 'none'; object-src 'self';" </IfModule>
Which is of course a lot unsafer as it only establishes the CSP for JavaScript and a little bit for CSS, but as the aim is XSS and core probably doesn’t have any embed/object stuff this might be considered (by someone with more experience than me).
Thus for the time being perhaps a browser condition might be helpful:
<IfModule mod_headers.c>
# global rule
Header set Content-Security-Policy "default-src 'self'; script-src 'none'; style-src 'none'; object-src 'none';"
# override for Safari PDF viewer case
Header set Content-Security-Policy "default-src 'self'; style-src 'unsafe-inline'; script-src 'none'; object-src 'self';" "expr=%{HTTP_USER_AGENT} =~ m#AppleWebKit(.*)Version(.*)Safari(.*)#"
</IfModule>
(The user agent detection at the back is necessary as “AppleWebKit” and “Safari” are also part of Chromes user string).
This is as far as my knowledge might help.
 Updated by Oliver Hader almost 4 years ago
Updated by Oliver Hader almost 4 years ago
Worked on an alternative here:
<IfModule mod_headers.c>
# matching requested *.pdf files only (strict rules block Safari showing PDF documents)
<FilesMatch "\.pdf$">
Header set Content-Security-Policy "default-src 'self' 'unsafe-inline'; script-src 'none'; object-src 'self'; plugin-types application/pdf;"
</FilesMatch>
# matching anything else, using negative lookbehind pattern
<FilesMatch "(?<!\.pdf)$">
Header set Content-Security-Policy "default-src 'self'; script-src 'none'; style-src 'none'; object-src 'none';"
</FilesMatch>
</IfModule>
 Updated by Gerrit Code Review almost 4 years ago
Updated by Gerrit Code Review almost 4 years ago
- Status changed from New to Under Review
Patch set 1 for branch master of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/67081
 Updated by Oliver Hader almost 4 years ago
Updated by Oliver Hader almost 4 years ago
@Alex can you please verify whether the references patch at review.typo3.org solves the problem you described? Thanks in advance for your feedback!
 Updated by Oliver Hader almost 4 years ago
Updated by Oliver Hader almost 4 years ago
- File Screen Shot 2020-12-10 at 14.25.16.png added
- File Screen Shot 2020-12-10 at 14.25.36.png added
 Updated by Oliver Hader almost 4 years ago
Updated by Oliver Hader almost 4 years ago
- File deleted (
Screen Shot 2020-12-10 at 14.25.16.png)
 Updated by Oliver Hader almost 4 years ago
Updated by Oliver Hader almost 4 years ago
- File deleted (
Screen Shot 2020-12-10 at 14.25.36.png)
 Updated by Oliver Hader almost 4 years ago
Updated by Oliver Hader almost 4 years ago
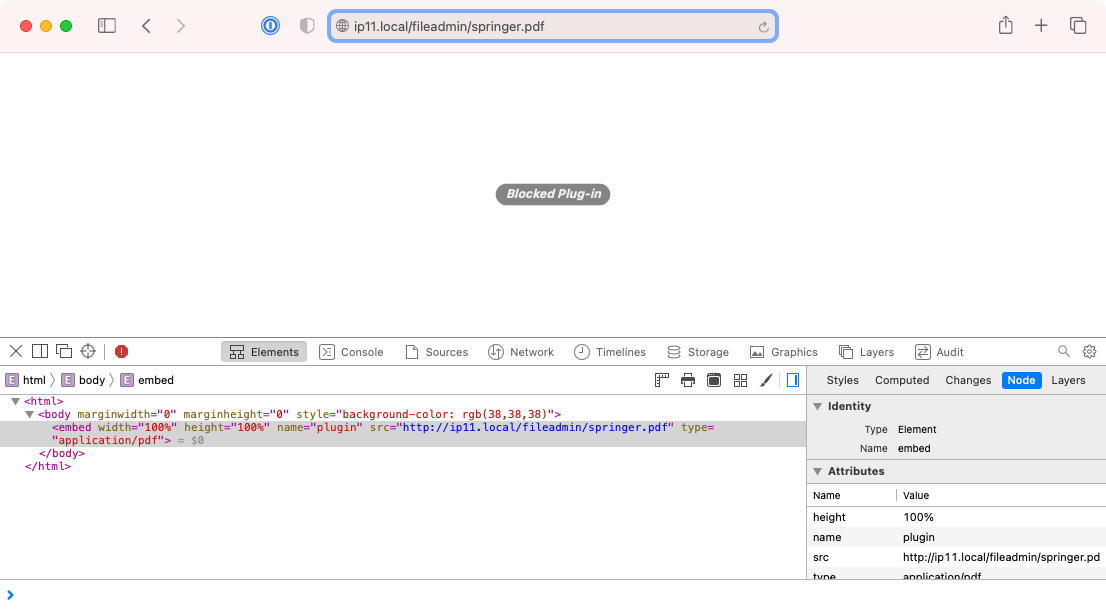
- File before_b.png before_b.png added
- File before_a.png before_a.png added
This is how it looked before this patch in Safari

 Updated by Alex Kellner almost 4 years ago
Updated by Alex Kellner almost 4 years ago
@Oliver: I have no idea how to work with review.typo3.org. Nevertheless I tested both configurations and both are working:
<IfModule mod_headers.c>
# global rule
Header set Content-Security-Policy "default-src 'self'; script-src 'none'; style-src 'none'; object-src 'none';"
# override for Safari PDF viewer case
Header set Content-Security-Policy "default-src 'self'; style-src 'unsafe-inline'; script-src 'none'; object-src 'self';" "expr=%{HTTP_USER_AGENT} =~ m#AppleWebKit(.*)Version(.*)Safari(.*)#"
</IfModule>
<IfModule mod_headers.c>
# matching requested *.pdf files only (strict rules block Safari showing PDF documents)
<FilesMatch "\.pdf$">
Header set Content-Security-Policy "default-src 'self' 'unsafe-inline'; script-src 'none'; object-src 'self'; plugin-types application/pdf;"
</FilesMatch>
# matching anything else, using negative lookbehind pattern
<FilesMatch "(?<!\.pdf)$">
Header set Content-Security-Policy "default-src 'self'; script-src 'none'; style-src 'none'; object-src 'none';"
</FilesMatch>
</IfModule>
 Updated by Gerrit Code Review almost 4 years ago
Updated by Gerrit Code Review almost 4 years ago
Patch set 1 for branch 10.4 of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/67087
 Updated by Gerrit Code Review almost 4 years ago
Updated by Gerrit Code Review almost 4 years ago
Patch set 1 for branch 9.5 of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/67088
 Updated by Oliver Hader almost 4 years ago
Updated by Oliver Hader almost 4 years ago
- Status changed from Under Review to Resolved
- % Done changed from 0 to 100
Applied in changeset 180bf9f69d6c73a47b2f7e4ad78973a162732402.
 Updated by Benni Mack almost 4 years ago
Updated by Benni Mack almost 4 years ago
- Status changed from Resolved to Closed
 Updated by Georg Ringer over 3 years ago
Updated by Georg Ringer over 3 years ago
- Related to Bug #93884: fileadmin/.htaccess (resources-root-htaccess) partially blocks SVG files added