Bug #103149
closedCSP prevents sitemap.xml inline CSS styles
100%
Description
Problem/Description¶
CSS Inline Styles in the auto generated sitemap.xml feature is blocked by Content Security Policy per default.
Affected: main, 13.0, 12.4
Acceptance Criteria¶
The styles should work without modifying CSP rules or the sitemap.xml template files.
BTW: what about a dedicated redmine category named "Content Security Policy"?
Files
 Updated by Timo Webler 9 months ago
Updated by Timo Webler 9 months ago
Our current workaround:
class PolicyMutatedEvent
{
protected string $sitemapPageType = '1533906435';
public function __invoke(\TYPO3\CMS\Core\Security\ContentSecurityPolicy\Event\PolicyMutatedEvent $event): void
{
$request = $this->getRequest();
if (
!$event->scope->isFrontendSite() ||
$request === null ||
$request->getAttribute('frontend.controller')?->getPageArguments()->getPageType() !== $this->sitemapPageType
) {
return;
}
$event->getCurrentPolicy()->set(
Directive::StyleSrcElem,
SourceKeyword::unsafeInline
);
}
protected function getRequest(): ?ServerRequestInterface
{
return $GLOBALS['TYPO3_REQUEST'];
}
}
 Updated by Benni Mack 8 months ago
Updated by Benni Mack 8 months ago
- Category changed from Frontend to Content Security Policy
 Updated by Timo Webler 8 months ago
Updated by Timo Webler 8 months ago
- Related to Bug #103567: Sitemap refuses to apply Stylesheet because of CSP added
 Updated by Oliver Hader 7 months ago
Updated by Oliver Hader 7 months ago
- Status changed from New to Under Review
- How to reproduce?
- What are the CSP headers being sent?
- What are the CSP violations being issued?
Besides that: Is it really relevant, that sitemap.xml supports styles when being shown in a browser? Or is it more like it should skip reports for sitemap.xml in case something is wrong there (but still block styles)?
 Updated by Timo Webler 7 months ago
Updated by Timo Webler 7 months ago
Oliver Hader wrote in #note-4:
- How to reproduce?
csp.yaml:
# Inherits default site-unspecific frontend policy mutations (enabled per default)
inheritDefault: true
mutations:
- mode: set
directive: 'default-src'
sources: ["'none'"]
- mode: set
directive: 'manifest-src'
sources: ["'self'"]
- mode: set
directive: 'img-src'
sources: ["'self'", "data:"]
- mode: set
directive: 'style-src'
sources: ["'self'", "'unsafe-inline'"]
- mode: set
directive: 'base-uri'
sources: ["'self'"]
- mode: set
directive: 'form-action'
sources: ["'self'"]
- mode: set
directive: 'media-src'
sources: ["'self'"]
- mode: set
directive: 'connect-src'
sources: ['self']
- mode: set
directive: 'script-src'
sources: ["'nonce-proxy'", "'self'"]
- What are the CSP headers being sent?
Content-Security-Policy: default-src 'none'; script-src 'nonce-JkAMWyZSCu6GhrHfwK6WLSPUIQC0vgunGZEmd-9RT1PpSpowF0zRfA' 'self' 'report-sample'; style-src-attr 'unsafe-inline' 'report-sample'; img-src 'self' data:; base-uri 'self'; frame-src 'self' *.youtube-nocookie.com *.youtube.com *.vimeo.com; style-src-elem 'self' 'nonce-JkAMWyZSCu6GhrHfwK6WLSPUIQC0vgunGZEmd-9RT1PpSpowF0zRfA' 'report-sample'; manifest-src 'self'; style-src 'self' 'unsafe-inline' 'report-sample'; form-action 'self'; media-src 'self'; connect-src self; report-uri https://exmaple.com
- What are the CSP violations being issued?
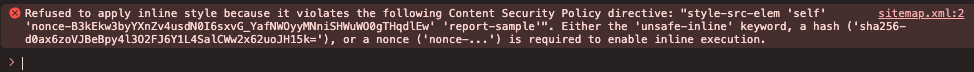
Besides that: Is it really relevant, that
sitemap.xmlsupports styles when being shown in a browser? Or is it more like it should skip reports forsitemap.xmlin case something is wrong there (but still block styles)?
Not really relevant. But TYPO3 deliver a stylesheet for that view and than it should work. Maybe remove the stylesheets for sitemap.xml as alternative solution.
 Updated by Oliver Hader 7 months ago
Updated by Oliver Hader 7 months ago
Thanks for the feedback, I was able to reproduce the behavior...
The resulting CSP violation looks like this:
{
"document-uri": "https://ip13.anyhost.it/?type=1533906435",
"referrer": "",
"violated-directive": "style-src-elem",
"effective-directive": "style-src-elem",
"original-policy": "default-src 'self'; script-src 'self' 'nonce-wdB5XPhMdnxXxfNpAsJGflt5UH0o_5-Z4ijHDwQLoQ-03gInUmWx_w' 'report-sample'; style-src-attr 'unsafe-inline' 'report-sample'; img-src 'self' data: *.ytimg.com *.vimeocdn.com; base-uri 'self'; frame-src 'self' *.youtube-nocookie.com *.youtube.com *.vimeo.com; style-src-elem 'self' 'nonce-wdB5XPhMdnxXxfNpAsJGflt5UH0o_5-Z4ijHDwQLoQ-03gInUmWx_w' 'report-sample'; report-uri https://ip13.anyhost.it/@http-reporting?csp=report&requestTime=1714503719476538",
"disposition": "enforce",
"blocked-uri": "inline",
"line-number": 2,
"source-file": "https://ip13.anyhost.it/",
"status-code": 200,
"script-sample": "body {\n font-fami"
}
script-sample gives an indication of what exactly caused the violation.
 Updated by Gerrit Code Review 7 months ago
Updated by Gerrit Code Review 7 months ago
Patch set 1 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Oliver Hader 7 months ago
Updated by Oliver Hader 7 months ago
- Related to Task #100887: Allow remote proxies to handle CSP nonce values added
 Updated by Oliver Hader 7 months ago
Updated by Oliver Hader 7 months ago
The patch at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099 is providing those hashes for the XSLT styles.
The hash value might be applied statically as well (sha256-d0ax6zoVJBeBpy4l3O2FJ6Y1L4SalCWw2x62uoJH15k=) - but I think this might be forgotten, in case the styles would be adjusted (even changing the formatting, whitespaces, etc. would require a new hash to be generated).
 Updated by Gerrit Code Review 7 months ago
Updated by Gerrit Code Review 7 months ago
Patch set 2 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review 7 months ago
Updated by Gerrit Code Review 7 months ago
Patch set 3 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Peter Kraume 5 months ago
Updated by Peter Kraume 5 months ago
- Has duplicate Bug #104125: CSP violation of Sitemap.xsl in XML sitemap added
 Updated by Garvin Hicking 5 months ago
Updated by Garvin Hicking 5 months ago
From dupe report #104125 a suggestion:
"Maybe by adding a check if CSP is off in the frontend and only then inserting the xsl?"
which has also been voiced here. The current patch seems to have stalled due to caching / performance implications.
Personally I do also think the stylesheet isn't that important to have, and we could just drop it when frontend CSP feature is active, instead of doing all this dynamic processing...?
 Updated by Gerrit Code Review 5 months ago
Updated by Gerrit Code Review 5 months ago
Patch set 4 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review 5 months ago
Updated by Gerrit Code Review 5 months ago
Patch set 5 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review 5 months ago
Updated by Gerrit Code Review 5 months ago
Patch set 6 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review 5 months ago
Updated by Gerrit Code Review 5 months ago
Patch set 7 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review 5 months ago
Updated by Gerrit Code Review 5 months ago
Patch set 8 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review 3 months ago
Updated by Gerrit Code Review 3 months ago
Patch set 9 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review about 2 months ago
Updated by Gerrit Code Review about 2 months ago
Patch set 10 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review about 2 months ago
Updated by Gerrit Code Review about 2 months ago
Patch set 11 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review about 1 month ago
Updated by Gerrit Code Review about 1 month ago
Patch set 12 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review about 1 month ago
Updated by Gerrit Code Review about 1 month ago
Patch set 13 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review about 1 month ago
Updated by Gerrit Code Review about 1 month ago
Patch set 14 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review about 1 month ago
Updated by Gerrit Code Review about 1 month ago
Patch set 15 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review about 1 month ago
Updated by Gerrit Code Review about 1 month ago
Patch set 16 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review 26 days ago
Updated by Gerrit Code Review 26 days ago
Patch set 17 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review 26 days ago
Updated by Gerrit Code Review 26 days ago
Patch set 18 for branch main of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/84099
 Updated by Gerrit Code Review 26 days ago
Updated by Gerrit Code Review 26 days ago
Patch set 1 for branch 13.4 of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/86824
 Updated by Gerrit Code Review 26 days ago
Updated by Gerrit Code Review 26 days ago
Patch set 1 for branch 12.4 of project Packages/TYPO3.CMS has been pushed to the review server.
It is available at https://review.typo3.org/c/Packages/TYPO3.CMS/+/86825
 Updated by Oliver Hader 26 days ago
Updated by Oliver Hader 26 days ago
- Status changed from Under Review to Resolved
- % Done changed from 0 to 100
Applied in changeset 937fbfe1365632c9965550fea0c33eb396bea106.